Lights Out! A Malware Perspective on the Iberian Power Failure
Tags:


Around 10:33 UTC, on April 28, 2025, Portugal, Spain, and some regions in the south of France were hit by a nationwide power outage. It impacted business, public transport, healthcare, and the daily lives of millions.
Considering Bitsight has its European headquarters in Portugal, our offices in Lisbon were no exception. Meetings got cut and cellular data quickly became unavailable due to the overflow of people trying to reach loved ones and some telecom providers prioritizing urgent communications. While some were prepared with UPSs, solar power, or batteries, some completely lost their ability to communicate with the rest of the world and live their normal lives. We went back to the old days, before television, where radios with batteries were the main news source for millions of people.
Thinking this could be a similar event as the pandemic, people rushed to the supermarkets to gather supplies, as we did not have a concrete power return ETA. Initial reports pointed to several days until the power was restored, and we even got some social media news that pointed to a state actor cyber attack from a reputable news outlet, which proved to be unsubstantiated. Hospitals started their power outage mitigation plans and managed to keep their power using diesel generators, while airports had to stop operations, leading to multiple people being unable to travel outside the country.
Slowly but gradually the power got restored; Spain had the advantage of having France and Morocco to re-synchronize their power lines and resumed power delivery more quickly, while Portugal had to rely on a black start (the process of restoring an electric power station) from two power plants to slowly return power to their territory. Eventually power returned to both countries, and by the end of the day, most—but not everyone—had electricity back to their homes. By the morning of April 29, power was finally restored, and everyone could once again rely on the technology that Thomas Edison and Nikola Tesla helped bring to the world.
While the exact root cause is still unknown at the time of writing, Spanish reports point to a sudden loss of 2.2 Gigawatts of power which triggered a failsafe mechanism. While this mechanism would work for smaller amounts, 2.2 Gigawatts was enough to have a cascading effect in Spanish and Portuguese power grids, which resulted in a complete blackout.
Using our own data we analysed the results this blackout had in our telemetry visibility (which we elaborate on in the next section) and how it impacted different organizations in both countries.
Internet backbone analysis
To provide wider context, we’ll start with a brief analysis of these countries' Internet Backbone, which is typically a reference to Internet Exchange Points, also commonly referred to as IXes or IXPs.These organizations are where internet service providers (ISPs), content providers, and large businesses connect to exchange data efficiently. While IXPs themselves don’t usually connect directly to other IXPs, the networks that participate in multiple IXPs create a web of interconnections that can be visualized as a graph. These links are established through a mix of commercial agreements and, in some cases, partnerships involving governments, academia, and businesses.

Considering IXPs’ participants are what actually provides internet access for each country, their aggregated telemetry provides a good representation of nationwide events like a power outage. We have analysed the traffic statistics for GigaPIX (the Portuguese Internet Exchange) and ESpanix (the Spanish Internet Exchange). This analysis reflects a dramatic decrease around 10:33 UTC on the 28th of April—or, the time when the nationwide blackout in these countries began.

Although one could assume the reason for the drop is likely just on end client devices, we decided to check if organizations that connect to each country's IXPs also got hit. Drilling down on each country's ASNs (Autonomous Systems, or entities that control IP address space) and announced IPv4/IPv6 prefixes, we also found a relevant drop on these countries for the blackout timeframe.

Using the information gathered so far we know there are some reasons for the loss of visibility:
- ASNs stopped announcing prefixes as they were not able to keep their systems powered, even if their clients have power and connectivity due to power redundancy systems.
- If the ASNs were able to keep up their systems, the sudden inflow of mobile clients could have resulted in a Denial of Service.
- Final users’ devices (or routers) lost their power as a consequence of being directly connected to the power grid, or their power redundancy systems run off.
Sinkhole data analysis
At Bitsight we maintain multiple sinkhole infrastructures to capture malware and potentially unwanted software telemetry. In our products, these are classified as Compromised Systems, Potentially Exploited, and Insecure Systems.
While we somewhat covered one of our Sinkhole infrastructures in the past for a particular malware family, today we will analyse the full data for Portugal and Spain. This, as you will find out below, has a direct correlation with the connectivity of systems on the internet in the case of a power outage.

While Compromised Systems and Potentially Exploited risk vectors are computed directly from malware telemetry, they differ depending on the different features of each malware family (although both impact our customers’ ratings).
For the purpose of this blog post we have compared April 28, 2025 and April 29, 2025 with the respective week-days for the previous week, yielding the following results:
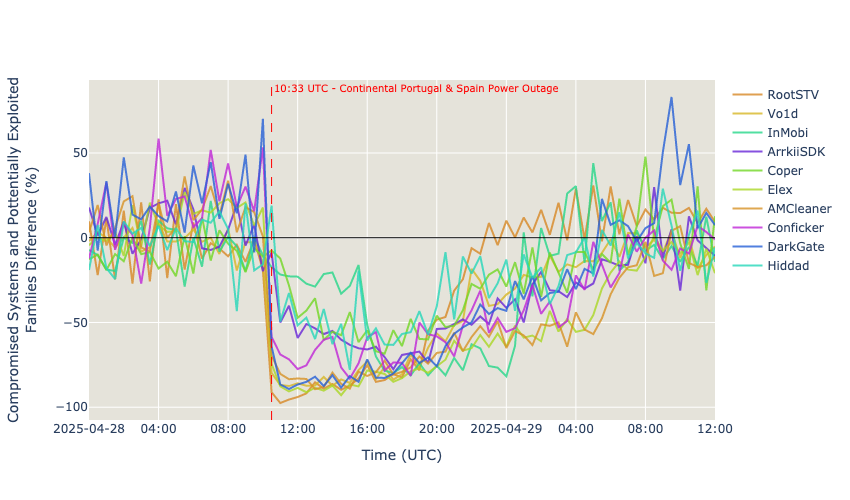
Top malware family differences with the previous week show an obvious pattern around 10:33 UTC, the time when the Iberian Peninsula got hit by the power outage; all families had a significant drop around this time. As expected, malware families that run on smartphones (like ArrkiiSDK) are not as expressive as the others, although we also are able to notice a slight decrease due to unavailability of some Mobile Operators. Around 19:00 UTC we notice a slow but steady increase of devices due to the return of power to various locations, and this continues until the next day. The positive difference values before 10:33 UTC are explained by the Spanish Easter Holiday on April 22, 2025 and many Portuguese that used holidays surrounding this date to take some days off, which resulted in lower traffic.
In the Insecure Systems comparison below, we notice a dramatic 1000% increase around 22:00 UTC. These are abandoned apps tied to smartphones like ColorOS and other devices that reached out en masse after their power was finally restored. Although slightly less evident due to the 22:00 UTC increase, a drop is also observable around 10:33 UTC, which is in line with the expected timeframe for the power outage.

Conclusion
Nationwide events like Portugal and Spain power outages, although rare, can significantly impact internet connectivity in these regions, ensuring geo-redundancy and disaster recovery plans should be the pillar of every medium to large organization. Companies outside of the Iberian Peninsula that relied on IPs within the prefixes announced by the affected ASNs likely had disruptions in their services (if they did not have geo-redundancy solutions in place) as well. Although cloud based providers can aid in implementing such solutions, a backup is only reliable if it can be tested beforehand and proved to work. Having multiple internet service providers can also help with disruptions, or at least ensuring critical communication continues uninterrupted. An organization is as resilient as their weakest link.
Malware is often dismissed as something to quarantine, or remediate, but it's worth remembering it can tell us something deeper: not just what got infected, but how infrastructure behaves under stress (or the lack thereof).
Taking the Iberian blackout as an example, the knocked out services caused a fair amount of chaos and disrupted the belief in something we take for granted. But it also made a digital footprint on malware visibility. And when we have footprints we just need to see how deep the rabbit hole goes.
Bitsight’s data gave us that vantage point, the kind of useful lookout that makes us many times believe we are just some meters ahead from many interesting conclusions. That we can use this to analyze macro-scale outages? That’s not just cool. That’s operational intelligence. And it’s sitting in our laps.
Not only malware telemetry gives you cybersecurity insights, but it can, for the creative mind, act as a lens. If you know where to look, and how to read it, it will quietly show you how the Internet breaks. Sometimes the best visibility comes from the most unexpected data.
Stay ahead of malware with Bitsight Pulse
Bitsight Pulse consolidates the latest cybersecurity news, ransomware events, and data breaches from hundreds of deep web, dark web, social media, and OSINT sources within a single screen or API feed, making sure you're always up to date on CTI news and updates. Talk to our team about getting started, or get a preview with our interactive product demo.